Malicious Software Removal Guide And Assistance
Before reading any further, make sure that you are running the latest versions of your current anti-virus and anti-spyware programs and ensure that the latest definitions are installed on your computer. Once you have updated all your anti-malware programs, please do a complete system scan with each program, one at a time. If you still encounter problems after doing this, please continue to read the rest of this page.
New and unknown viruses and spyware are stubborn and difficult to remove from a computer system. This page provides detailed instructions on how to remove malicious software from your computer. Please do not be overwhelmed by all the information and steps on this page. Getting rid of malicious software is not a simple task and involves a lot of software installations, configurations, scans and headaches, but we have tried to make the process as simple as possible. Up to this point you may ask: "I am no computer expert, what if I am unable to remove these infections from my computer?" You are not completely alone during this process, at the bottom of this page you will find instructions on how to generate a special report, called the HijackThis log, that you can send to us for analysis as a final resort. We will analyse this report and reply with a possible solution, or we will refer you to people who can help if we are unable to resolve your problems.
It is very important that you follow all of the steps on this page very carefully before sending us your HijackThis log. The HijackThis log is intended for unknown infections that you are unable to detect or remove after using all the removal methods available to your disposal.
We want your feedback about this page, whether it is positive or negative. Help us make this page more user-friendly. Visit our contact page to send us your feedback.
Step 1: Download and install a secure secondary web browser (Firefox)
If you do not experience any annoying pop-ups or redirects in your current browser, you may skip this step. However, it is advised that Internet Explorer users switch to an alternative browser that is not integrated into the operating system and one that is able to operate independently from Internet Explorer, for example Mozilla Firefox.
Chances are good that your browser is hijacked if you are infected with spyware. This will complicate the cleanup process of your computer because constant pop-ups and redirects will make it hard to download the software required to clean your computer. We recommend you download and install Firefox for more secure browsing. When you are asked to make Firefox your default browser, it is extremely important that you select No (Refer to Step 11 of our Firefox Installation Guide). We do not want the malware to know that you are using another browser and want to give them the idea that you are still surfing the Internet with your current browser. Installing Firefox is very easy and straightforward, but our Firefox Installation Guide is a step-by-step instruction guide designed especially for users not familiar with software installations. If you are already using Firefox, download and install Opera. Remember to select No when Opera asks you to make it your default browser.
Note: Installing a secondary browser without making it the default browser will NOT change any settings in your current default browser. You will still be able to use your current default browser just like you did in the past. If you accidentally made another browser your default browser, simply open your original browser and click on Yes when it prompts you to make it the default browser.
Step 2: Download our recommended anti-virus and anti-spyware software
Below are links to the latest versions of the software you will need to disinfect your computer. Do not attempt to install the software at this time, we only need you to download the setup files for each application at the moment. If any of the software listed below is already installed on your computer, please make sure that you have the latest version of each program and that their databases are up to date. Simply download the software not yet installed on your system and remember where you put the files. Please note that all the programs listed below are completely free of charge.
- [Anti-virus] AVG Anti-virus Free Edition by Grisoft
- [Anti-spyware] Ad-Aware Free Edition by Lavasoft
- [Anti-spyware] AVG Anti-Spyware by Grisoft
- [Anti-spyware] Spybot - Search & Destroy by Patrick M. Kolla / Safer Networking Limited
Step 3: Disconnect your computer from the Internet and any other network
Before we install the software you downloaded, you need to physically disconnect your computer from the Internet and any other network you may be connected to, by unplugging your modem, network cable and any other cable connecting you to the Internet or any other network. You need to make it impossible for viruses, trojan horses, worms and spyware to call for backup once you start to dismantle them. They will continue to infect your computer with new variants while you are connected to the Internet. We also need to prevent hackers from controlling your system and they will try to prevent you from removing the pests they installed on your computer.
Step 4: Disable or un-install your current anti-virus software
You will be required to install other anti-virus software than the one you are using at the moment and running two anti-virus programs simultaneously can cause conflicts on your system and make it unstable. An unstable system is to the advantage of viruses and spyware and we do not want to give them any advantage at the moment. If you are not already using the anti-virus software recommended in Step 2, please un-install your current anti-virus software or alternatively, disable its resident shield before installing our recommended anti-virus software. (Consult the support documentation of your current anti-virus software for instructions on how to do disable its resident shield).
Step 5: Install and configure the software you downloaded
Now it is time to install the software needed to clean up your computer. Install each of the applications you downloaded at Step 2. Do not attempt to update the software at this moment. We want to enable as much protection as possible before reconnecting to the Internet. The anti-virus and anti-spyware software may start to detect infections on your computer once it is installed. Allow the software to quarantine or delete the detected infections. Do not worry if it is unable to remove certain infections at the moment, we will do a complete scan of your system a little later and tackle each stubborn infection one-by-one.
Step 6: Update your anti-virus and anti-spyware software
Now you will need to reconnect your computer to the Internet so that we can make sure that you have the most up to date database installed for each of your malware removal programs. Most programs have an update button, option or link located in the main application window of the program. Simply click on this button, option or link and follow the instructions or prompts on your screen to update the software.
Step 7: Scan your computer with the software you downloaded
Disconnect your computer again from the Internet and any other network and restart your computer into Safe Mode.
We recommend you do a quick scan at first and then a complete system scan, one program at a time. Scanning your computer with several programs simultaneously, will cause file access conflicts. Make sure that the anti-virus/anti-spyware scanner is the only program open at this time. Close the windows of any other programs before initiating a system scan. Allow each program to quarantine or remove all the infections it discovered during the scan.
VERY IMPORTANT NOTE: Please restart your computer after each scan. Some scanners schedule infected files for deletion when the system is restarted. A malicious process cannot be deleted while it is active in your system, to terminate a stubborn process you need to reboot your system. The scanner will then attempt to delete the malware on the next reboot, before it loads itself into the memory again.
Once you completed scanning and cleaning your computer with all the programs listed in Step 2, you may reconnect your computer to the Internet and any other network it was connected to. Remember to keep your anti-virus and anti-spyware software updated at all times, scan your computer regularly and keep your resident shields running at all times. With all the active threats on the Internet these days, you cannot afford letting your guard down.
If you are still infected after scanning your computer with our recommended software, please continue to read the rest of this page.
Some infections require special attention. No anti-virus or anti-spyware program is able to remove every malware infection, especially new variants not yet identified by anti-malware developers. However there are a couple of specialised malware removal tools that are updated on a regular basis, making them highly effective against specific infections. Visit our Special Malware Removal Tools page for more information.
For a comprehensive list of online malware scanners, please visit our Online Malware Scanners page.
Tip: Enter the names and file names of the infections from the report, generated by the online malware scanner, into the search boxes below to search for possible solutions of similar infections on other websites.
If the anti-virus and anti-spyware software deliver no results, and you know the name of the malicious software causing the problems on your computer, type the name followed by the word "removal" into a search engine like Google and click on Search. For instance if you are infected with the Storm worm, type "storm worm removal", or "storm virus removal" in the search box. If you don't know the name of the infection, type the error or warning messages appearing on your screen, the name of the product appearing through constant popup windows, or the name of the file that's causing the problem. You can also search our Malware Sample Database or compare a suspicious file on your system, against the samples stored our database.
Now that you have tried almost everything and can't seem to find the solution to your problem, visit a Malware Removal Forum and ask for assistance. Visit our Malware Removal Forums page for more information.
IMPORTANT: Do not send us your HijackThis log if you haven't yet scanned your computer with the software listed in Step 2, scanned your computer with the Kaspersky Online Virus Scanner and if you haven't yet asked for assistance on at least one of the sites listed on our Malware Removal Forums page.
If you are still stuck with the malicious software after following all the advice given above, follow the 4 simple steps outlined below. We will analyse your HijackThis log and respond with a possible solution. This will also allow us to identify which files and objects are causing the problems on your computer.
** Please note that our response time to your query depends on our workload **
** and the number of viruses and spyware reported to us for analysis. **
Requirements For Using This Service
Many people jump to the final resort without following the abovementioned instructions and advice. We provide these steps for a reason, because it is senseless and a waste of valuable resources to assist people in the manual removal of infections that can anyway be removed with conventional malware removal software and tools.
Please understand that these rules are for your own good, for the sake of everyone else using this service and will ensure fast and effective attention to your problem. So before you scan your system with HijackThis, please follow these basic rules:
- Ensure that all the programs recommended in Step 2 are installed on your computer. You may already own an anti-virus or anti-spyware program that you paid for, but the mere fact that you got infected with malware already shows that your current anti-malware software are either outdated or not capable of removing the malware threat.
- People sometimes send us a short message explaining the problem without including a HijackThis log. We are going to ask for it anyway, so please make sure you include your HijackThis log, otherwise you will not receive a reply.
- Please remember to include the report of the Kaspersky Online Virus Scanner, we will not reply to your e-mail if you fail to do this. This report reveals certain infections not shown in a HijackThis log.
- If you used any of the special malware removal tools, please include those reports as well, if possible.
- Please supply us with the links to the topics on the malware removal forums where you received assistance. There is no merit in suggesting methods that are not working, so we need to know what have been done so far to address your problem, which methods worked and which ones did not. We also do not want you to repeat any steps already taken. You are required to ask for assistance in at least one of these forums before sending your HijackThis log to us. If you did not join one of these forums, it means you did not follow our instructions and you will therefore not receive a reply.
- If you have complied with all these requirements, please proceed to Step 1 below.
Step 1: Download HijackThis
We recommend that you create a folder on your hard drive called HJT and download the file to this location (C:\HJT). If you are not familiar with the creation of folders, visit the following page for instructions: How to Make a Safe Windows Folder to Run HijackThis. This page will also explain why you need to download HijackThis to a permanent location.
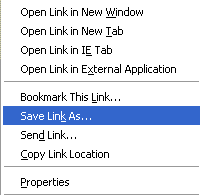
Download the latest version of HijackThis. To download HijackThis right-click HERE and click on Save Link As... (For Internet Explorer users: Save Target As..) as illustrated in the figure below.
The Save As window will appear after this. Now choose the folder you just created (C:\HJT) and click on the Save button, like illustrated in the figure below.
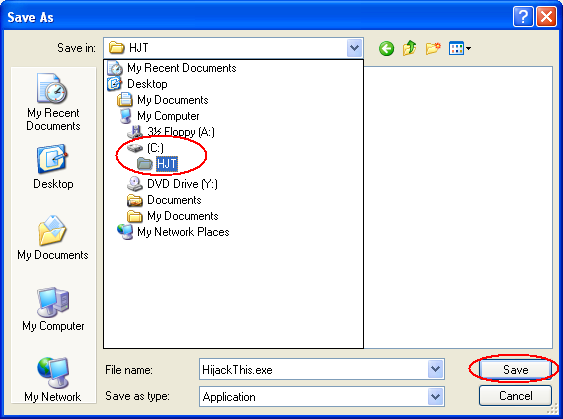
Wait for the download to finish and proceed to Step 2.
Step 2: Run HijackThis
Open the file named HijackThis.exe either by double clicking on it from the location where you saved it, or by clicking on Open on the Downloads box (if the Downloads box closed after the download, go to the Tools menu and click on Downloads, or press J while holding down the Ctrl key). Refer to the figure below.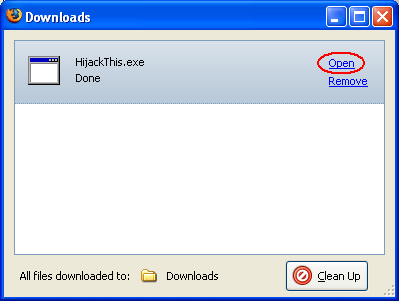
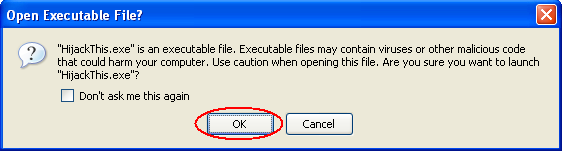
If you get a warning message about executable files containing viruses and malicious code that could harm your computer, click on OK. HijackThis is safe and does not contain any viruses. The warning message should look like the one indicated in the figure below: (Please note that this is a safety feature of Firefox and you should never click on OK unless you are sure you can trust the executable file to be launched)
Click on "I Accept" once the Trend Micro End User License Agreement appears and wait for the following screen to appear:
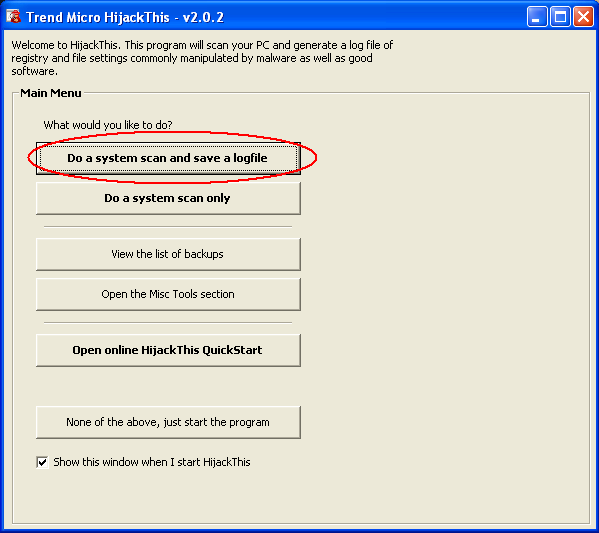
Step 3: Scan your system with HijackThis and generate a logfile
Now click on the first button that reads, "Do a system scan and save a logfile". Notepad should open after the scan with a report containing the results of the scan, looking more or less like this (note that the contents of this report will vary from system to system):
Step 4: E-mail us your HijackThis log
- Right-click within the Notepad window containing the results and click on Select All, right-click again and click on Copy.
- Click HERE to create a new e-mail message (if the link does not create a new e-mail message, use our contact page to send us the information).
- Paste the copied text into this e-mail (go to the Edit menu and click on Paste, or press the Insert key while holding down the Shift key).
- Attach the Kaspersky Online Virus Scanner report, or copy and paste its contents into the e-mail as well.
- Remember to include your links to the Malicious Software Removal forum topics where you received assistance.
- Please attach or paste the contents of the reports from any special malware removal tool as well.
- Include a short description at the bottom of the e-mail, explaining more or less what is wrong with your computer.
- Click the Send button to send us the e-mail.
If you know which file is causing the problem, please submit it to us through our Malware Sample Submission Form.
Now you can close all the windows you have opened during this process. Do not attempt to fix any of the results reported by HijackThis, unless you know what you are doing.